As we’ve been outlining in our ransomware blog series, protecting against a ransomware attack requires a multifaceted defense strategy that covers and supports multiple layers of infrastructure. Each layer of infrastructure requires its own unique level protection — endpoint, server, and network, along with backup and disaster recovery. In this post, we’ll look at how to best prevent a ransomware attack from spreading to your server infrastructure.
Let’s start by referencing the same best practices we mentioning for endpoint protection: take a holistic approach that requires prevention of known bad code from being accessed in the first place and then preventing it from running. It’s no longer sufficient to just look for known bad files and block them. The same methodology and approaches apply to server protection. You are looking to establish a “hub” to examine intent, implement security policies, and centrally configure and monitor everything. Transparency and insights are the key before acting. This is where multi-cloud firewall protection comes in.
Multi-Cloud Firewall Protection
When an endpoint device (think a laptop, a desktop workstation, a tablet, or a phone) has been compromised the malware will target your server infrastructure next. The software will try to exploit a weakness (through security vulnerabilities in the operating system or applications on your endpoints) and attempt to spread over the network. Once inside your network, the ransomware will begin to encrypt files on the target system and attempt to encrypt files on any drives or any connected device that the infected machine can write to.
At this point in a ransomware attack, further damage can still be prevented. You have network traffic between external connections and internal workloads (north & south) and traffic between servers (east & west). The compass analogy helps to explain how you’ll need to protect network traffic from every direction. A multi-cloud firewall solution can help augment all security points on a network (device & servers) protecting ingress and egress traffic so that attackers can’t get in and data doesn’t leak out.
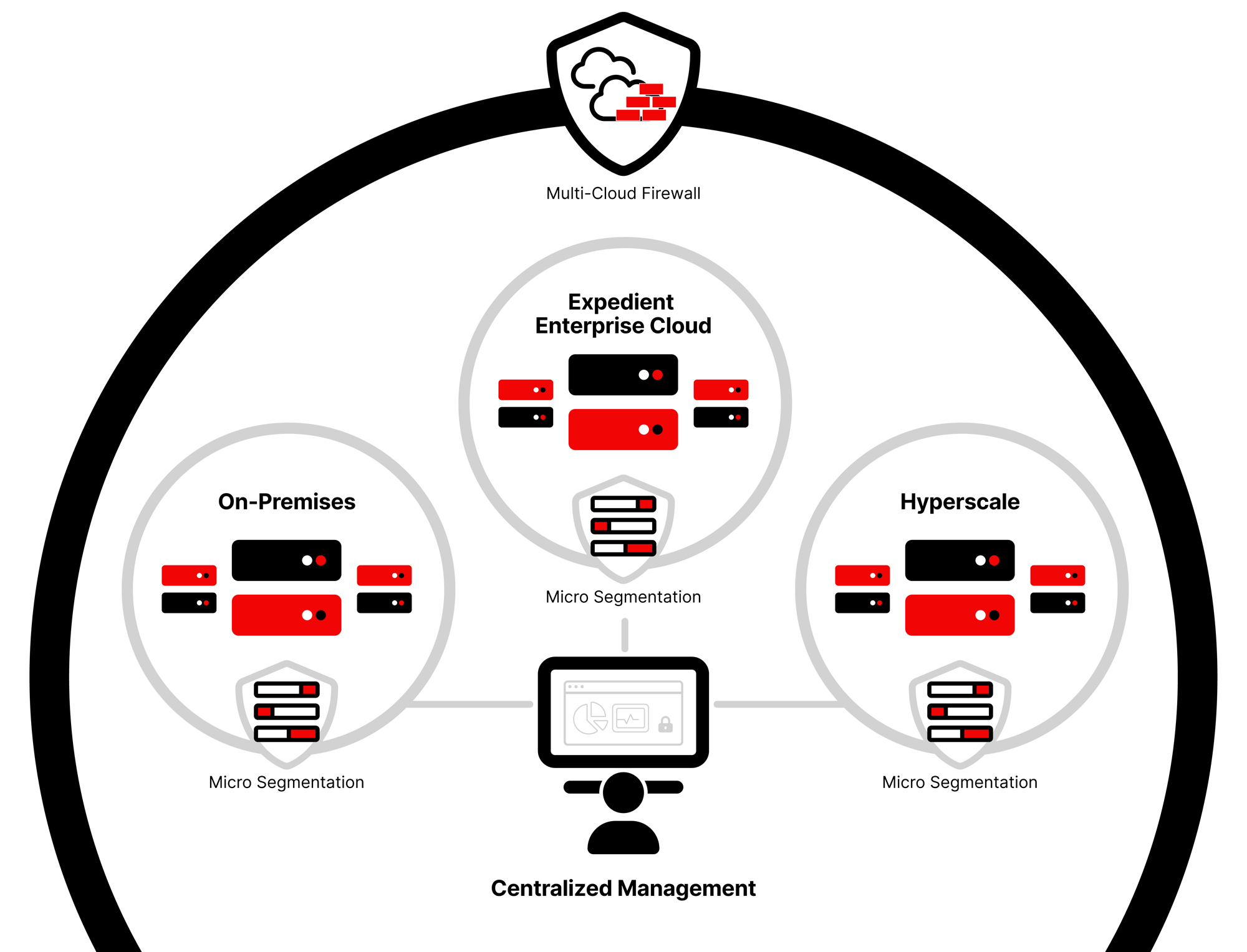
Firewall protection should not be siloed to be effective. You need a unified view of all data from firewalls across your organization including those deployed at third-party clouds, such as AWS and Azure so you can enforce attack detection and prevention policies at the firewall and application level. The firewall can report suspicious links and then sinkhole or quarantine the machine before anything dangerous happens.
At Expedient, we offer firewall protection using WildFire, which identifies threats from the industry’s largest enterprise malware analysis community, including threats submitted from the network, endpoint, cloud and third-party partners.
Microsegmentation
Microsegmentation﹣the act of isolating workloads from one another to prevent infection from within a network﹣is another part of our ransomware server prevention strategy. With proper microsegmentation, you can authorize applications to talk to one another and prevent unauthorized communications laterally. microsegmentationIf an attack is detected, you can quarantine a server or endpoint device which slows malware spreading between the servers themselves (east to west traffic).
Microsegmentation should also be designed into logical segments (business units or departmental resources or geographies). This will help contain the impact of any intrusion affecting the organization and prevent or limit lateral movement of bad actors and malware both. By properly segmenting your users from your server/network infrastructure, you’re able to add another level of protection to detect the malware and isolate it.
Hopefully this has given you some insights into how to stop the spread of ransomware on your server infrastructure. Next, I’ll be explaining how disaster recovery and data backup are essential to mitigating the risks of any ransomware attack and a look at how to plan for a worst-case scenario. In the meantime, let me know if you have any questions experts@expedient.com.
