The headlines just keep piling up! In the past few weeks, we’ve seen ransomware attacks continue to wreak havoc on supply chains and disrupt services. The latest round of casualties includes JBS, the world’s largest processor of fresh beef and pork, Colonial Pipeline, the U.S.’s largest refined-fuel pipeline operator, and Ireland’s HSE, which provides public health and social care services, all falling victim to ransomware attacks.
At this point, few would argue that ransomware has become a “global pandemic” (as former director of the Cybersecurity and Infrastructure Security Agency Chris Krebs puts it), with no end in sight. Gangs of cybercriminals have even become so bold as to advertise their services on the dark web, collaborating to share code, infrastructure, techniques, and profits. It is even being acknowledged as a threat to national security.
In my first blog, I explained what a ransomware attack is and how it spreads. Now let’s talk about best practices for endpoint devices. Endpoint devices include desktops, laptops, tablets, mobile phones, and other devices that connect to a corporate network, while servers provide the raw computing to run applications and store data. Both are vulnerable to ransomware attacks, in different ways, but can be protected by deploying very similar methods.
Protecting Users from Themselves
The most common way ransomware spreads is via email or phishing scams because of the way they exploit employee/human vulnerabilities. They operate by having criminals impersonate legitimate organizations via email, text message, advertisement, or other means to fool users into opening the door. Just one bad click or download and the dominos can begin to fall. A best practice and way to safeguard against such an attack is to implement a system of email scanning and advanced firewall protection capabilities to prevent malware from even knocking on your door.
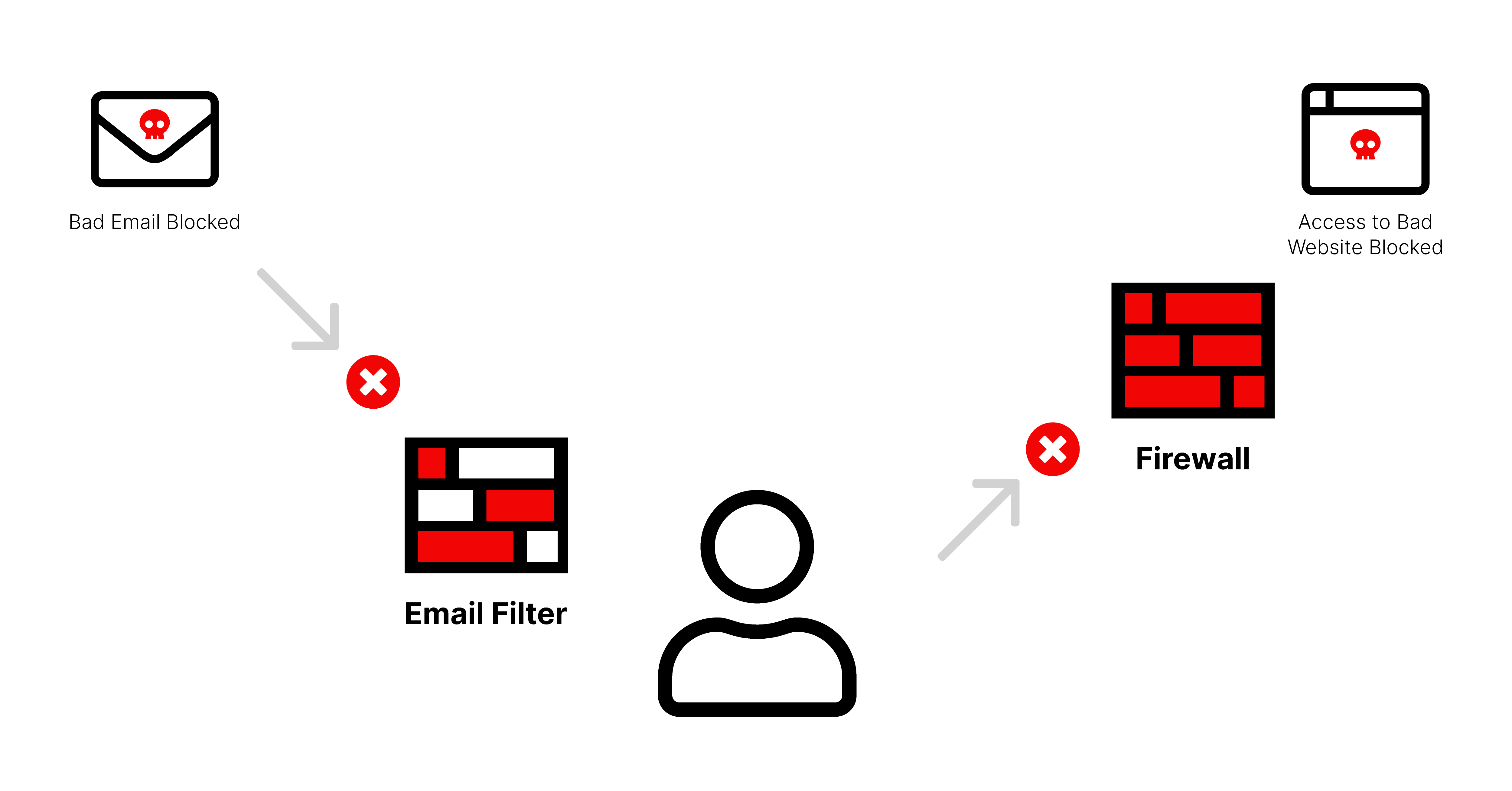
Email filters help detect and block unwanted emails from ever reaching employees. They work by reading emails, opening attachments, and tracking every link to analyze the data for malicious content. It blocks dangerous files and malicious links from reaching employees, preventing the opportunity for an employee to make a mistake.
In addition to email scanning, a firewall that uses website reputation intelligence helps protect employees from accessing malware sources and malicious or inappropriate content on the Internet, typically via a web or URL filtering solution. As an example, if you’ve ever tried to access a web page at work and gotten a “website blocked” notification, your company is using web filtering.
This way, administrators and security teams can block a variety of content on the way in and prevent access to malicious content.
Looking for “Bad” Behavior
Being able to detect and notify bad user behavior is critical to any ransomware defense.
There are three key areas of focus for this: behavioral detection, access control, and micro-segmentation.
This is where Expedient can help with a modern behavioral-based detection and response solution. If ransomware can’t get its foot in the door, it can’t take hold of your business. Additionally, properly controlling access to applications through a robust identity and access management policy and solution further reduces the chances of an initial infection. Finally, a robust micro-segmentation strategy can make it much more difficult for an attack to spread, should it find a way in the door. All three of these areas of focus share a common goal – explicitly grant access to known good entities (i.e., code execution, network paths, or access policies) and block everything else by default. We’ll talk more about network protection in a later post.
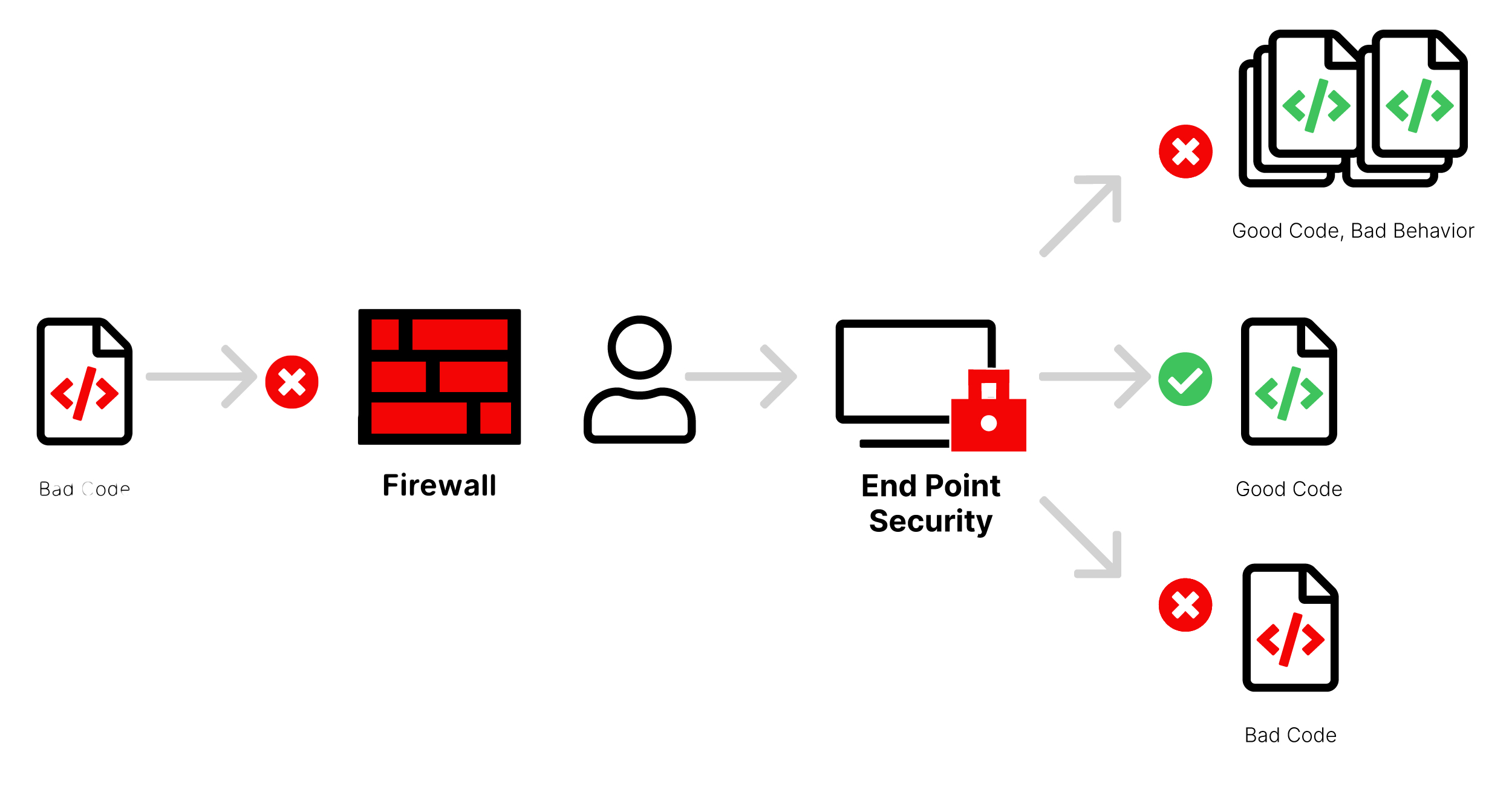
Preventing Malicious Code from Executing
The next step is a firewall to scan all incoming traffic and keep malicious code from entering the network using automated sandbox analysis. If the malicious code is able to sneak past that scan, endpoint security can prevent the code from running and potentially spreading.
By explicitly allowing only known good code to run and preventing it from being used maliciously, you can prevent many ransomware attacks from starting or spreading.
Go Beyond the Tools
While utilizing best-in-class technology can help prevent attacks, your people and processes also need to be tuned to prevent ransomware attacks from spreading. One common way to do this is to utilize the Principle of Least Privilege for granting access to systems. By keeping access needed to the absolute minimum, you can prevent user accounts from being compromised and used to slip past defenses. This is especially common in spearphishing attacks that target IT administrators to use their accounts to access and exfiltrate personally identifiable information. Additionally, all access and activity should be logged to monitor for anomalous activity.
A Multi-Layered Approach
The big takeaway from all this is that protection from a ransomware attack needs to be layered like an onion. You need protection and security at every level—endpoint devices, network, servers, and data backup. Hopefully, this has given you some insights into how to defend the periphery and endpoints of your network. In my next blog post, I’ll take a deeper look at how to protect your servers and network from a ransomware attack. In the meantime, let me know if you have any questions: experts@expedient.com.
